I. Introduction
Earlier, we have basically completed the myblog project using native nodejs, let’s learn how to protect the security of our project…
sql injection: steal database content
XSS attack: Stealing front-end cookie content
Password encryption: to ensure user information security (important!)
We only focus on prevention at the web server (nodejs) level
Two, security
1. SQL injection attack
The most primitive and simplest attack, since there is web2.0, there has been sql injection attack
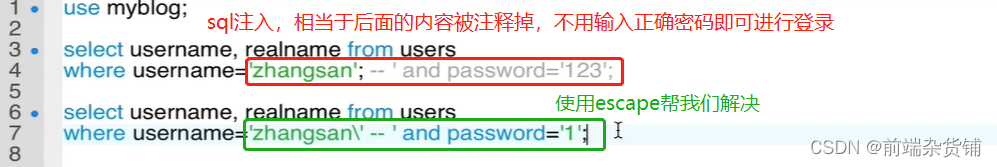
Attack method: input a sql fragment, and finally splicing it into a piece of attack code
Precautions: Use mysql’s escape function to handle input
Modify the export content of the ./db/mysql.js file
mysql.js
module.exports = {
exec,
escape: mysql.escape
}
1
2
3
4
Modify the content of the ./controller/user.js file
user.js
Add escape to the imported module, add escape before the user name and password, and then remove the quotation marks of ${} in the sql statement
// Change
const { exec, escape } = require(‘../db/mysql’)
// login (by username and password)
const login = (username, password) => {
// Change
username = escape(username)
password = escape(password)
// Change
const sql = `
select username, realname from users where username=${username} and password=${password}
`
console.log(‘sql is’, sql)
return exec(sql).then(rows => {
return rows[0] || {}
})
}
// export share
module.exports = {
login
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
twenty one
At this point, the problem of sql injection can be solved…
2. xss attack
Attack method: Doping js code in the page display content to obtain web page information
Precautions: convert special characters for generated js
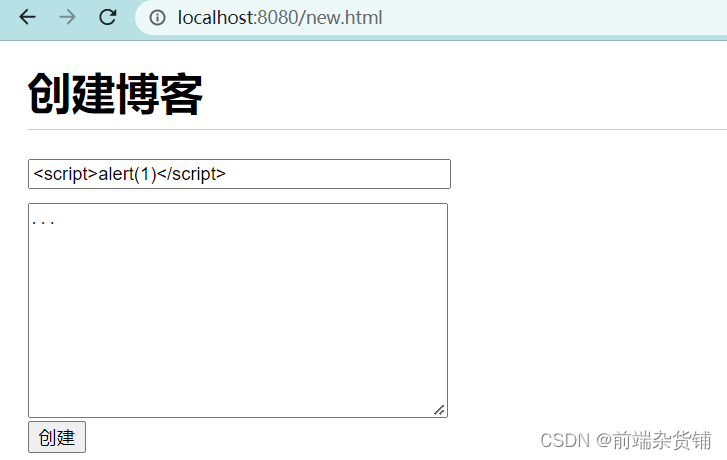
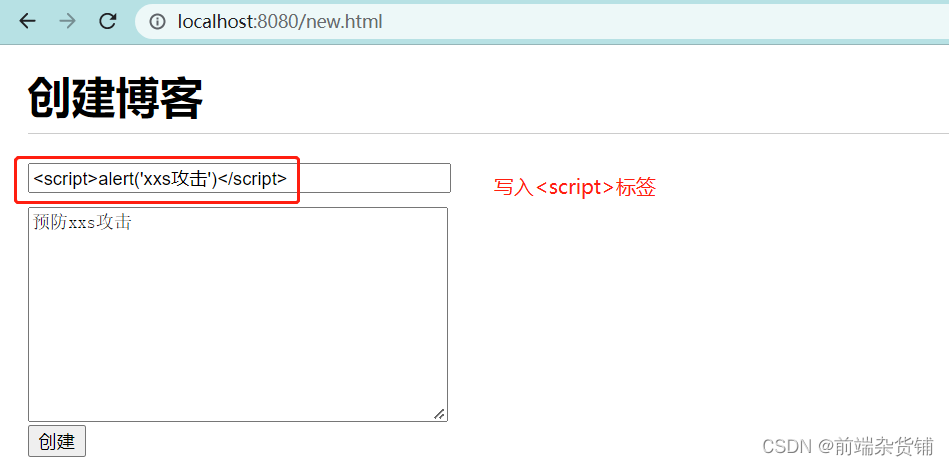
When we do not prevent xxs attacks, for example: enter <script>alert(1)</script> in the input box of creating a blog, it will execute
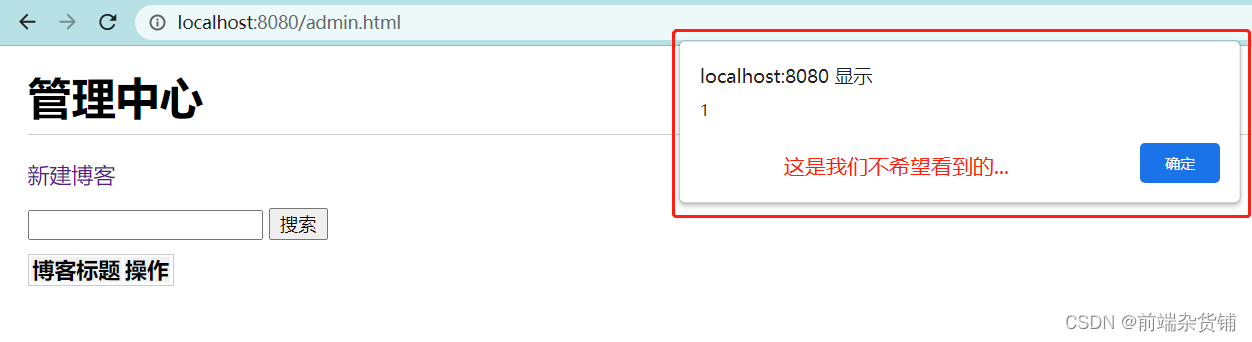
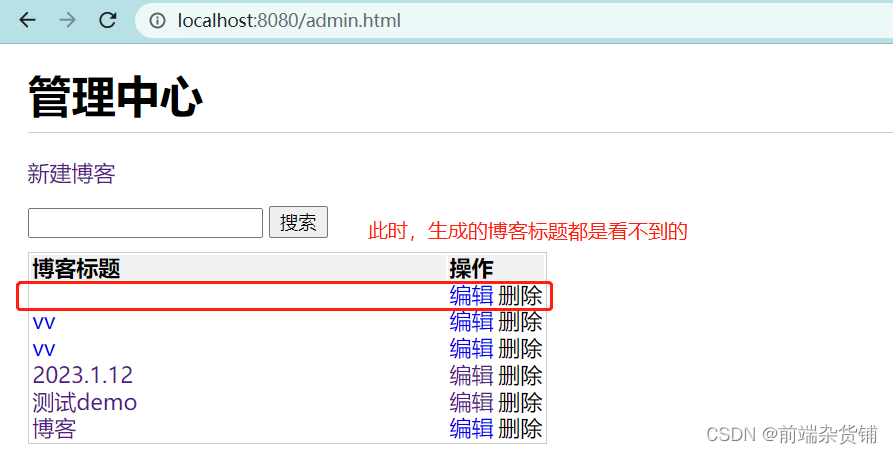
So how do we solve it? First, install the xxs tool
npm i xxs
1
Then modify the code of the .controller/blog.js file
blog.js
Import xss and use it in title
const xss = require(‘xss’)
…
const newBlog = (blogData = {}) => {
// blogData is a blog object, including title content author property
const title = xss(blogData. title)
…
}
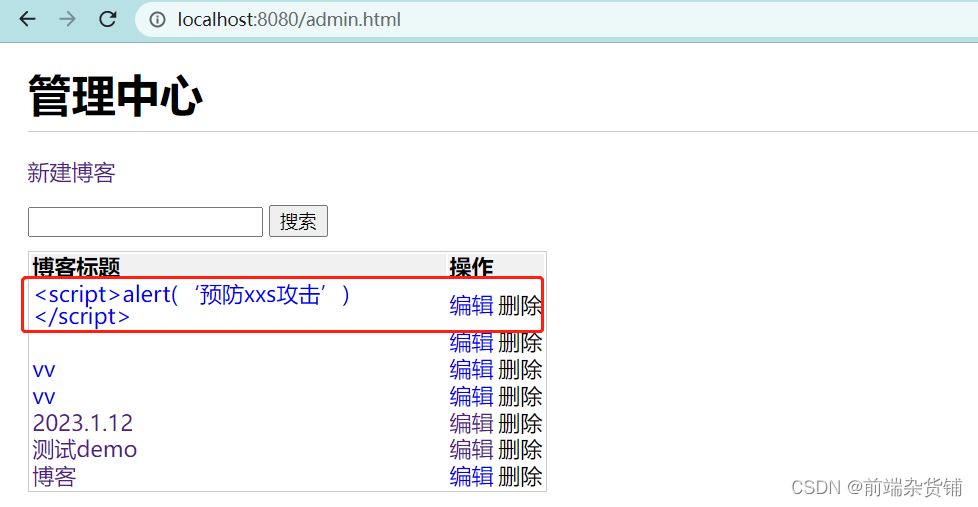
3. Encryption algorithm
In case the database is compromised by users, the last thing that should be leaked is user information
Attack method: Obtain the user name and password, and then try to log in to other systems (because many people’s passwords will be reused in different places)
Precautions: Encrypt the password, even if you get the password, you will not know the plaintext
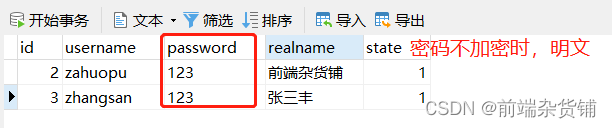
So how do we solve it? —— Use the crypto library provided by nodejs
Create a new cryp.js file in the utils.js file for encryption algorithm
crpy.js
We use md5 encryption (a type of encryption)
// encryption library
const crypto = require(‘crypto’)
// key (a key, the password and the key are encrypted together)
const SECRET_KEY = ‘Zahuopu_2023#’
// md5 encryption (an encryption method)
function md5(content) {
// create md5 encryption
let md5 = crypto. createHash(‘md5’)
// Return the encrypted result of the input content in hexadecimal
return md5.update(content).digest(‘hex’)
}
// encryption function
function genPassword(password) {
// The string should contain password and SECRET_KEY
const str = `password=${password}&key=${SECRET_KEY}`
return md5(str)
}
const result = genPassword(‘123’)
console. log(result)
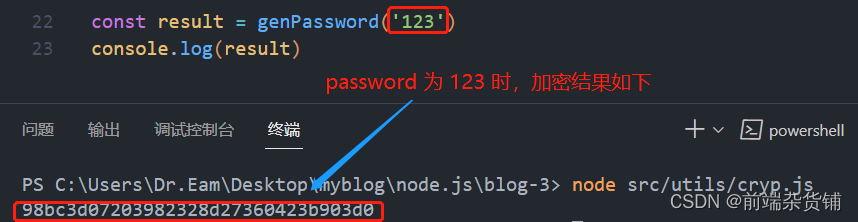
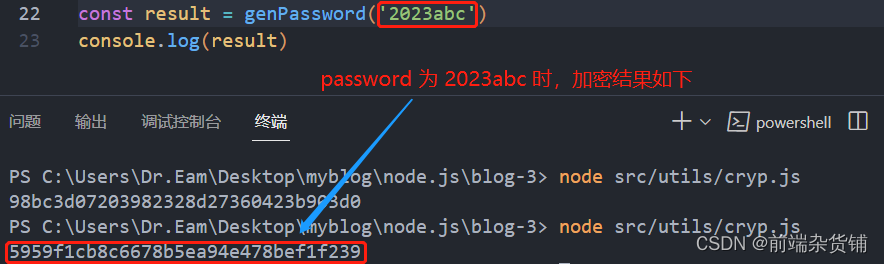
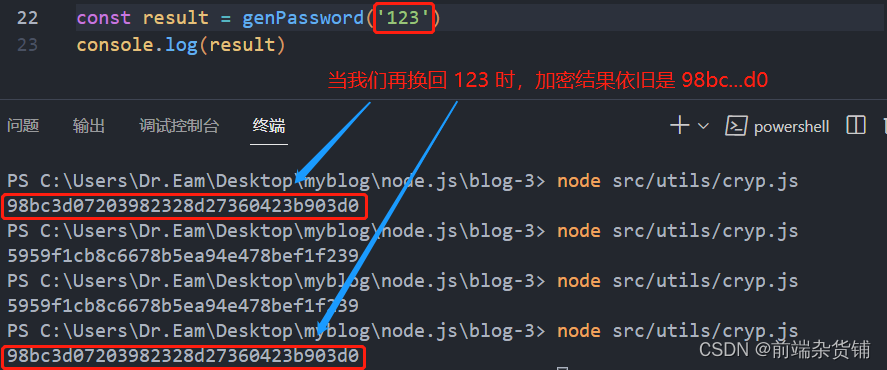
It can be found that our encrypted password is 32 bits
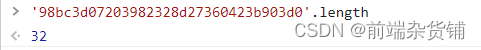
Then we have to modify the length of the password in the database to 32 bits
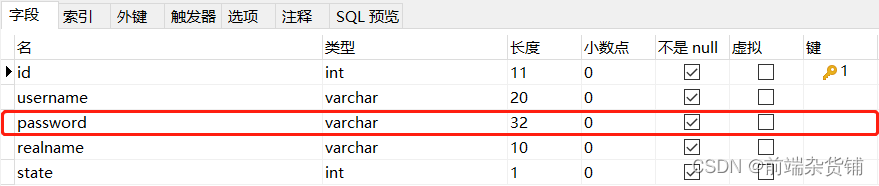
Next, let’s change the password of the user zahuopu in the database
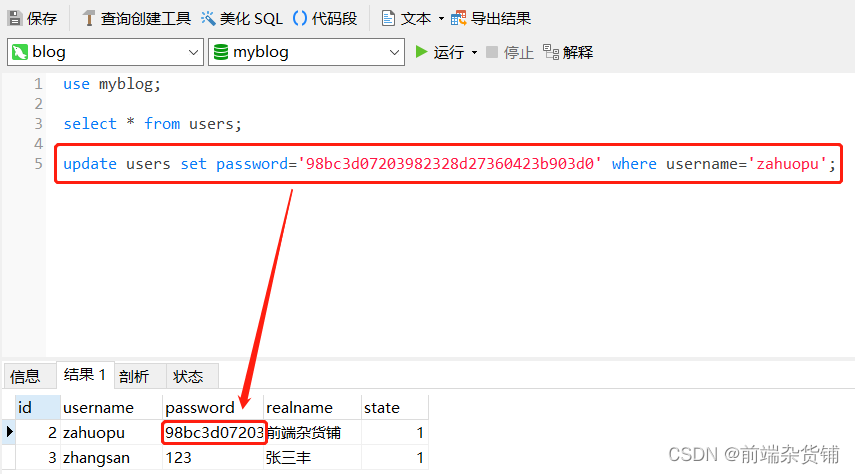
4. Use encryption algorithm
First we export the encryption algorithm
cryp.js
…
module.exports = {
genPassword
}
1
2
3
4
5
Then we modify the content of ./controller/user.js
user.js
const { exec, escape } = require(‘../db/mysql’)
const { genPassword } = require(‘../utils/cryp’)
// login (by username and password)
const login = (username, password) => {
username = escape(username)
// generate encrypted password
password = genPassword(password)
// Changed the location of this code a bit, it will be used immediately in sql to prevent sql injection
password = escape(password)
const sql = `
select username, realname from users where username=${username} and password=${password}
`
console.log(‘sql is’, sql)
return exec(sql).then(rows => {
return rows[0] || {}
})
}
// export share
module.exports = {
login
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
twenty one
twenty two
twenty three
twenty four
After returning to the login interface, you can log in successfully