1. Common terms
1. APK file
It is the abbreviation of Android Package, which is the Android installation package. In fact, the APK file is presented in the form of a compressed package. By directly transferring the packaged APK file to the Android emulator or Android phone for execution and installation, various APP programs we use are formed.
2. APK file directory
assets: This directory stores resource files that are not compiled by appt.
lib: All so files are stored in this folder.
META-INF: This folder stores the signature file of the apk
res: This folder contains resource files.
AndroidManifest.xml file: It is a configuration file, which contains the declaration and configuration of components.
classes.dex file: It is an executable file that can run directly on the Android system.
resources.arsc file: It is a file generated after aapt packs the resource files in the res directory.
For example:
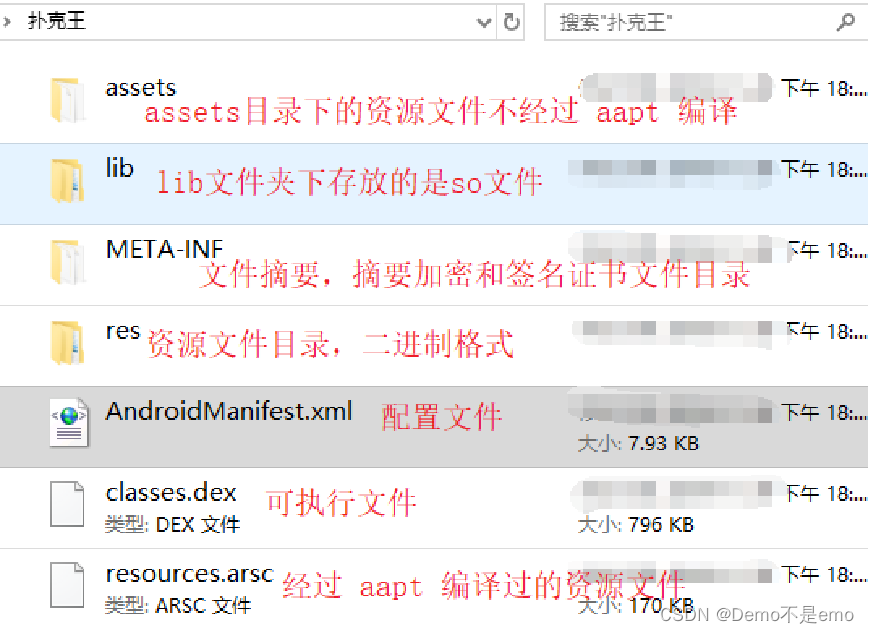
[1], META-INF folder
In the META-INF folder: This folder contains the apk signature file, open it, we can see that it contains three files:
CERT.RSA file: signature certificate file, which stores the public key and encryption algorithm description
CERT.SF file: Digest encryption, which stores encrypted files. It is the ciphertext information obtained by encrypting the digest plaintext with the private key. Only the public key paired with the private key can decrypt the file.
MANIFEST.MF file: the file summary, which stores the program manifest file, which contains the summary plaintext of all files in the package.
[2], res folder
In the res folder: This folder contains resource files, which are files compiled by appt:
The folder at the beginning of drawable: pictures and xml files are stored in it.
layout folder: all layout files are stored in it.
There will also be a menu folder in some APKs: the menu files are stored in it.
anim folder: stores animation files,
color folder: stores color files,
mipmap folder: It also stores image resources.
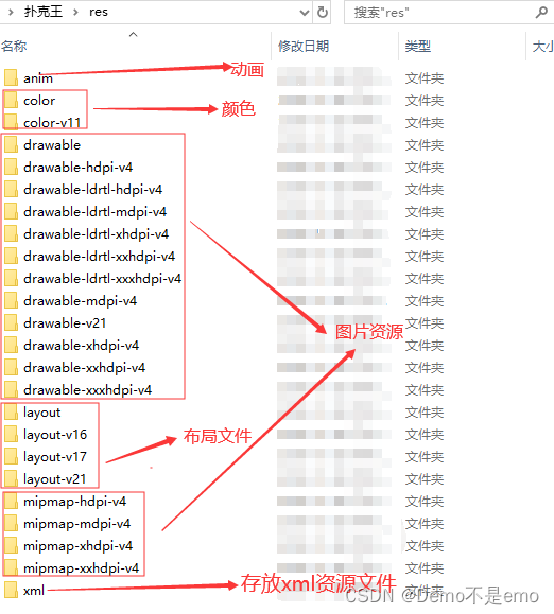
2. Apk packaging process
3. Introduction and use of adb
ADB (Android Debug Bridge), ADB is a tool in the Android SDK, with which you can directly operate and manage Android emulators or real Android devices. The original intention of Android is to use a tool like ADB to assist developers to debug APK faster and better in the process of developing Android applications, so ADB has the following functions:
Install and uninstall apk
Copy push file
View device hardware information
View application resource usage
Execute shell commands on the device
As for the installation of the adb tool, I won’t talk about it here. A blog will be released later to introduce adb in detail. The related toolkit can also be obtained from me. After the installation is complete, the following interface will appear. echo
Here is just a brief demonstration, let me show you the commonly used commands
adb common commands
adb devices: Displays currently connected devices
adb install: installation package path
adb shell dumpsys activity top Get current active interface information
adb shell dumpsys package [packagename] Get package information
adb shell dumpsys meminfo [pname/pid] Get memory data
adb shell dumpsys dbinfo [packagename] to get the database file
adb shell pm list packages lists all currently installed package names
adb shell pm path [packagename] Get the path where the specified program is located
Here I open a thunderbolt simulator to demonstrate to you, as follows, enter the following command to see which devices are connected to adb
adb devices
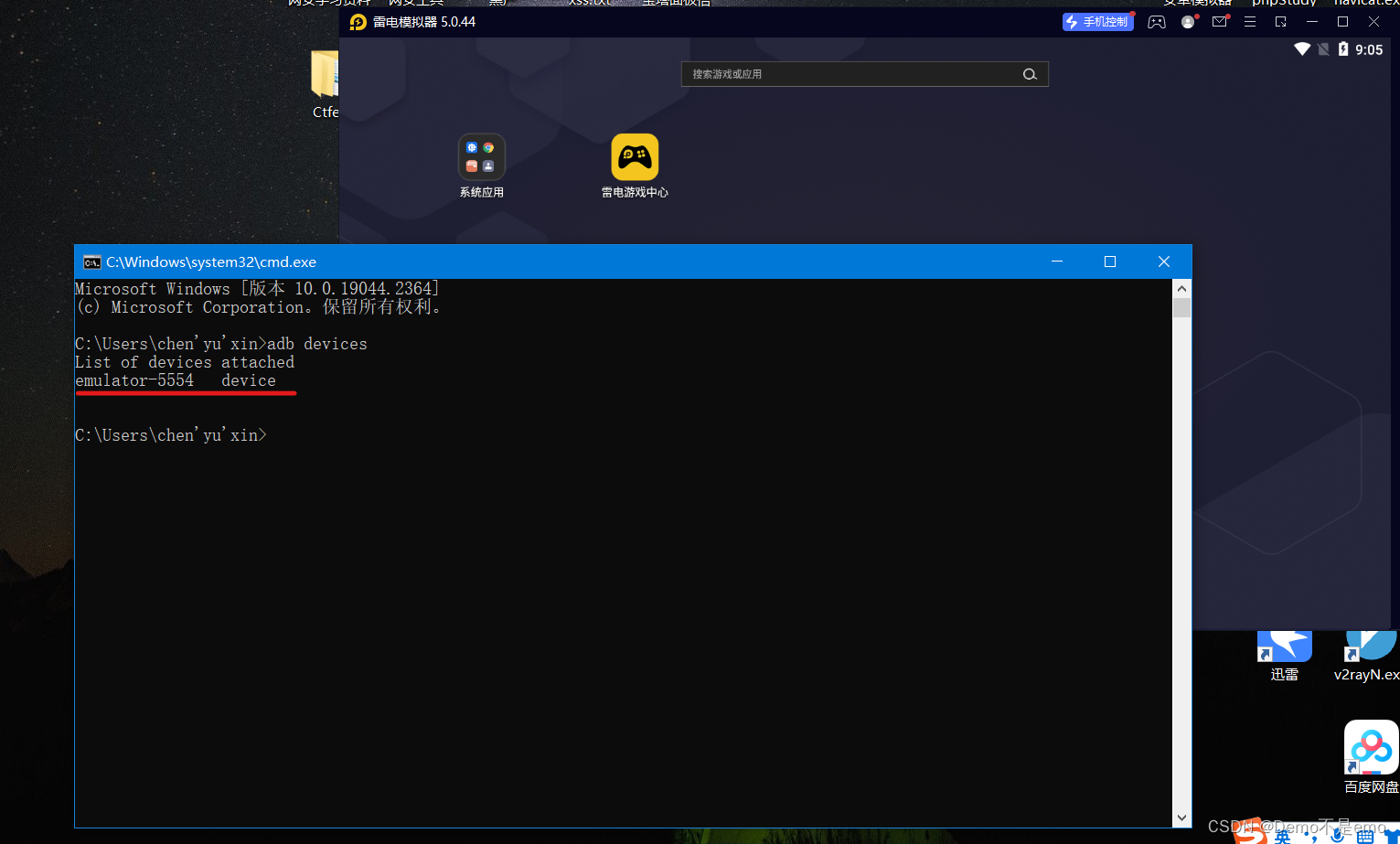
You can also enter his shell terminal and directly enter
adb shell
That’s it, the effect is as follows
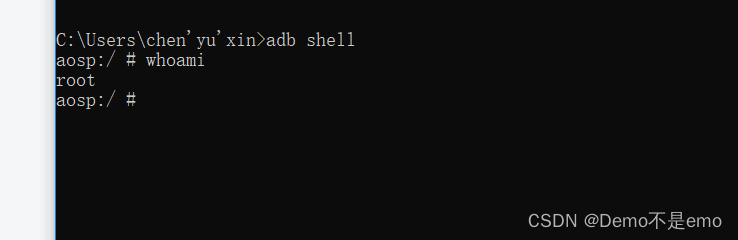
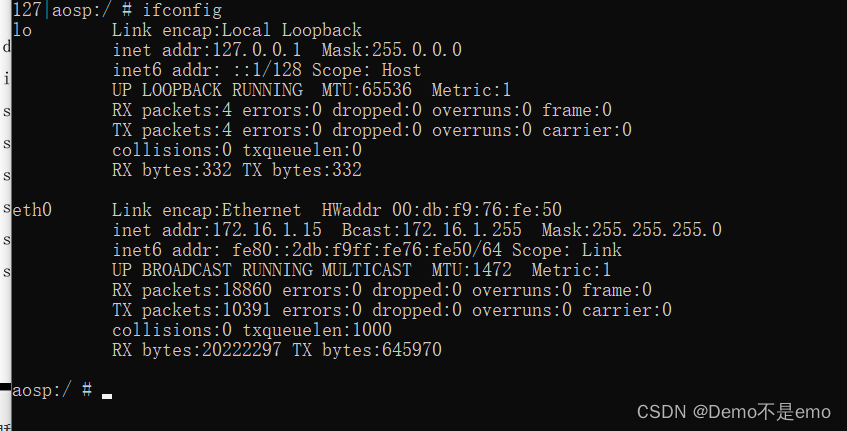
You can also see that you are now the root user. The shell command here can directly use the Linux command ”, which is almost the same, such as checking the ip address
Another example is to install the prepared apk file for the connected device, as follows
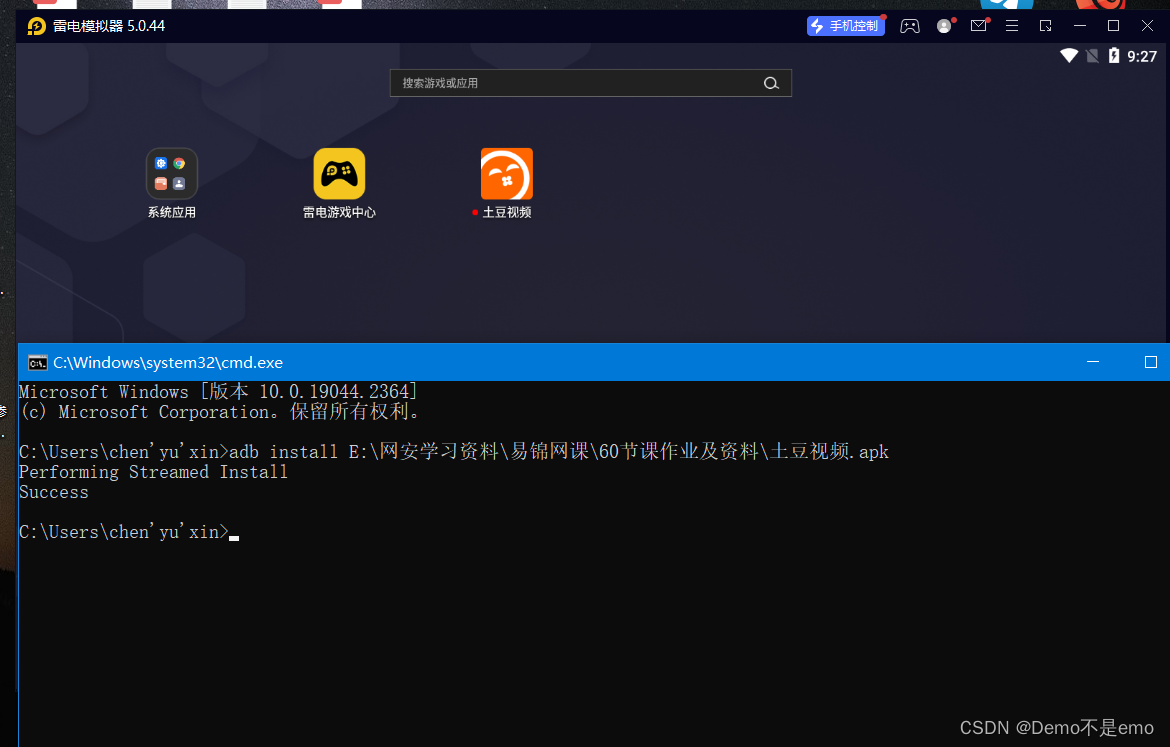
Later, I will demonstrate his debugging effect in detail, and a blog will be published to introduce this tool in detail.
Some ideas based on infiltration are that when other people are charging your computer with a usb device, directly install the apk Trojan file prepared in advance for him, or just handle it directly (without any bad wizards), so learn Infiltration should connect all the knowledge points you have learned to infiltration, and combine the knowledge points.




